With every webpage loaded, email sent, or video streamed, network traffic takes a complex journey…
In today’s interconnected world, where network performance is crucial for business operations, understanding the significance of ICMP (Internet Control Message Protocol) becomes paramount. Today’s post sheds some light on the critical role of ICMP and why it should not be disabled despite legacy security concerns. By implementing proper security measures, businesses can leverage the benefits of ICMP while mitigating potential risks.
A Problematic Story
Imagine being an employee for a considerably sized corporation who is tasked with being highly productive from home for any variety of common reasons. You sit down at your computer with the intent of accomplishing a list of tasks and attending meetings using several apps from Microsoft 365, Salesforce, and custom cloud apps.
You log into the company network remotely, only to wait several seconds that stretch far longer than expected. All your apps lag when you open them, and by the time you’re ready to work, it’s already close to your first meeting, and you haven’t even completed some initial, easy tasks, or even reviewed the meeting notes, all because everything is so slow.
Now expand this scenario to all remote employees. Then expand it to employees who work from the office. Additionally, workers at remote job sites, or those traveling, experience these persistent issues. Executives are more than annoyed. With the advent of faster internet connections, remotes users and cloud and SaaS systems should enable everyone to work faster than ever.
At least, that’s the expectation.
But how to troubleshoot the problem?
One answer might be to leverage monitoring with traceroute (or, really, Service Watch) to troubleshoot where in the network there is a slowdown. However, the more likely underlying problem is that inspecting the network path for performance issues requires ICMP. Many IT personnel incorrectly consider ICMP to be riddled with security holes. In years past, indiscriminately disabling ICMP seemed like a safe idea when all client <=> server traffic was internal. But now, with more dependencies on hosted cloud, SaaS, and external services, disabling ICMP seems like a giant shot in IT’s foot.
Why is this often-over-looked protocol so important? Is ICMP a security risk and a danger? Should it be disabled? How can ICMP be leveraged to diagnose network issues? It may be time to take a deeper look at the importance of the Internet Control Message Protocol and reevaluate the perceived risks.
Historical Security Concerns
A variety of security issues have been used as a reason to forego usage of ICMP including the following:
- ICMP Attacks
The primary concern is the possibility of a “ping of death” attack that floods a network with echo request packets, causing system crashes. However, modern firewalls can detect and prevent such attacks, ensuring network operability is maintained. - ICMP Tunneling
ICMP tunneling can be used to bypass firewall rules, but it is worth noting that other protocols like HTTPS and DNS can achieve the same objective. Disabling ICMP entirely is an inadequate solution, and organizations should prioritize implementing comprehensive security measures that address risks across various protocols. - Network Scanning
Ping sweeps and floods are often used to scan networks for identifying hosts. However, firewalls have the capability to eliminate these threats. Disabling ICMP does not solve the underlying network issue but deprives administrators of a valuable troubleshooting tool. - ICMP Forged Redirects
ICMP forged redirects can enable man-in-the-middle attacks by sending fraudulent redirects to an attacker’s IP. However, modern firewalls have robust security measures in place to protect against such attacks. Disabling ICMP is a shortsighted approach that restricts network monitoring with unnecessary security tactics.
ICMP is Necessary – More Than Ever
While concerns exist regarding ICMP’s security risks, these can be effectively managed with modern firewall technology. Disabling ICMP altogether is unnecessary and can hinder network troubleshooting and performance optimization efforts. Instead, organizations should implement capacity and security measures that address risks across multiple protocols.
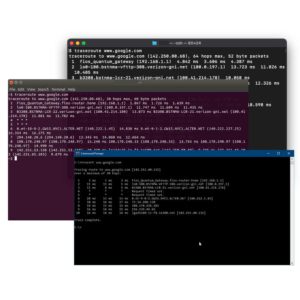
Indeed, many Active Directory-based organizations now must allow ICMP simply for the domain usage. Common ping and other communication between host sources and end-user devices is integral to Active Directory. Or, with the advent of SaaS and web-based technologies and hybrid work support, network monitoring is now more essential than ever. Expanded monitoring that improves user experience becomes an imperative. Given these reasons, it’s important to reconsider ICMP’s importance and how it can be leveraged to meet the advancing workplace needs no matter where that may be and no matter what solutions are used.
The Benefits of ICMP
ICMP offers several benefits beyond troubleshooting and monitoring network errors. Organizations should focus on securing their networks while making effective use of ICMP to enhance network efficiency and reduce latency.
- Troubleshooting and Monitoring
ICMP aids in identifying and resolving network errors, from latency issues to service outages. Ongoing monitoring of ICMP data improves uptime and enhances user experience, especially for remote users. Disabling hampers troubleshooting efforts and impedes receipt of crucial information such as TTL messages. - Efficient Traffic Routing
ICMP provides important network packet information so routers properly direct network traffic for the best available paths, minimizing latency and optimizing network performance. Disabling ICMP redirects impedes efficient traffic routing and negatively impacts user experience.
Best Practices
Instead of blocking ICMP entirely, organizations should focus on securing their networks while leveraging the benefits of ICMP. Robust security measures, including advanced threat detection capabilities in firewalls, can mitigate potential risks.
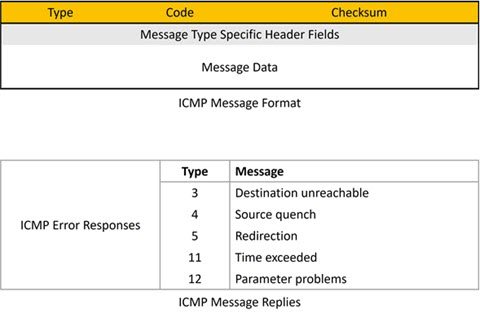
The following ICMP packet types are important for functional ICMP responses across an organization’s networks to provide appropriate monitoring of devices and a variety of application types:
- Type 11 packets for time exceeded responses must be allowed by the firewall for traceroute to work, providing useful network troubleshooting and monitoring.
- Type 8 and type 30 packets provide echo requests and information requests respectively, both of which are outbound packets and not a security issue.
- Type 0 packets will affect the TTL of traceroute responses, addressing MTU issues already discussed, if this is otherwise disabled.
Type 3, code 4 packet responses will also improve MTU response effectiveness tot larger packets across a hybrid network where timely remote user-affected packet responses are imperative for positive experience enhancement.
Monitoring is the Key Ingredient
Organizations should not disable ICMP completely, but instead, implement robust security measures and make effective use of the protocol for network management and performance monitoring. ICMP is crucial for troubleshooting, monitoring, and optimizing network performance, enabling organizations to thrive in a connected world.
Monitoring is important for security, uptime, and productivity. By leveraging ICMP and using solutions like Exoprise’s Service Watch, organizations can maximize network performance while delivering exceptional user experience. Service Watch provides vital information to keep any size organization functioning at peak levels.
In the next post, we will explore how Exoprise’s monitoring solutions leverage ICMP to rapidly diagnose network performance issues. We will delve into the importance of ICMP for ping, traceroute, Windows and macOS and how Exoprise’s products utilize low-level technology and algorithms to improve monitoring.